Cryptology Annual News Update and Vignette
Bill Ricker
for BLU.org
Sept 21, 2022
Cryptology News Bulletins 2021-09 to 2022-08
Certificate Authority Root problems
Let’s Encrypt Root CA Expiration
https://community.letsencrypt.org/t/production-chain-changes/150739
Rich Pieri via lists.blu.org Fri, Oct 1, 9:34 PM
to discuss
Some CA bundles like the one distributed with Sylpheed for Windows
contains several expired CA certs including the now expired
DST Root CA X3 certificate.
This can cause problems with Let's Encrypt certificates
even though the bundle has the ISRG Root X1 CA cert.
Rot8000
ROT8000 is the Unicode equivalent of ROT13. What’s clever about it is
that normal English looks like Chinese, and not like ciphertext (to a
typical Westerner, that is).
-Shneier
web
app
commentary
not as easy to do in shell or Perl/Python as Rot13 !!
PGP Fit for purpose?
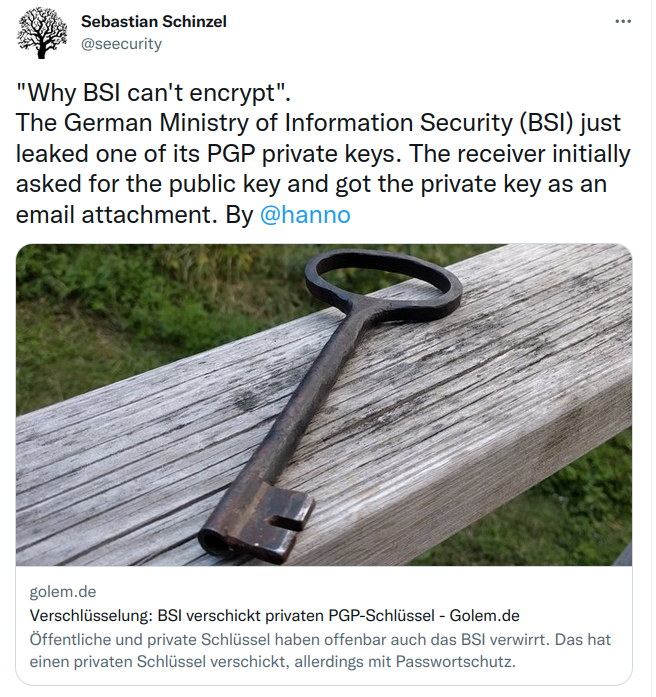
Sebastian Schinzel @seecurity
“Why BSI can’t encrypt”.
The German Ministry of Information Security (BSI) just leaked one
of its PGP private keys. The receiver initially asked for the
public key and got the private key as an email
attachment.
Don’t treat this as a failure of BSI people. They are good people.
It’s more like “PGP is so shitty that even the BSI screws it up
badly”.
c/o
Stephan Neuhaus @stephanneuhaus1 Nov
16, 2021
Cryptography is a machine for turning any problem into a key
management problem.
deleted so anonymous
PGP is a program which turns cryptography into an arsenal full of
foot-guns
Crypto News Feature: Post Quantum Cryptography
What’s Quantum Computing?

Quantum
Superposition when used for computing.
- QC measured in “qubits” not bits
- 30% True, 70% False.
Kinds of Quantum Hardware
We’re discussing PQC before QC?
Yes !
Quantum
Cryptography
- theoretically using entangled quantum states
- to create an encryption
- or an anti-eaves-droppable connection
What’s the problem?
- Unbreakable ciphers aren’t always unbreakable, for always.
- QC could theoretically break most PKI
- Schor’s Algorithm / Grover’s / VQF
- discrete log as well as prime factoring, even elliptic curves
Generalization of Forward
Secrecy
NIST’s Post-Quantum Cryptography Standards
The goal of post-quantum cryptography (also called quantum-resistant
cryptography) is to develop cryptographic systems that are secure
against both quantum and classical computers, and can interoperate with
existing communications protocols and networks. –
NIST
NIST PQC Competition
National Institute of Standards & Technology started a
multi-round competition, similar to with AES and SHA3 competitions
NIST PQC Selections for 2022
NIST
PQC 2022-08-16 July
5th 
- PKE/KEM (PKI key exchanges)
- CRYSTALS-KYBER
“Cryptographic Suite for
Algebraic Lattices”
- DSA
- CRYSTALS-DILITHIUM
(uses variant of SHA-3)
- FALCON
- SPHINCS+
- Round 4 - further research for additional PKE/KEM
- BIKE
- Classic McEliece
- HQC
- SIKE †
† and weeks later into Round 4, SIKE
was broken. Badly.
1 core-hour.
Well, that was
^further research^.
So when can i play?
The plan is to roll out these new PQC ciphers as additional cipher
options in TLS. Soon?
- Experiments have been tried with hybrid PKE/KEM/DSA (layered
classical PKI & PQC) with TLS.
- Google is planning
roll-out (with CloudFlare?).
- MS has a PQC
project including PQ
TLS which is helping OQS OpenQuantumSafe with a PQC-enabled
fork of OpenSSL.
- Digicert is co-backer of several candidates with Google
- Google’s BoringSSL
support also
- German Federal OIS targeting Kyber in
Thunderbird.
NIST PQC Schedule
- 2022 Fourth NIST conference is Nov 29 - Dec 1 (CFP deadline Oct
1).
- 202⅔ Draft Standards Available
- 2024 FIPS Standards;
FIPS Allowed.
- 202⅚ FIPS certification for the PQC algorithms;
FIPS Approved.
Known weaknesses
- breaks have eliminated 62 of 69 entrants in Rounds 1 to 4
- including the two front-runners, Rainbow and SIKE
- 7 remain, will they survive?
- FALCON would be compromised by a lack-of-randomness in salt, or
failure to salt, as repeating same key and hash again gives too much
information.
Isn’t that an unlikely
compromise?
No. It’s happened.
- numerous implementations have failed to salt encryption of small
data despite warnings.
- DEBIAN broke system random which compromised many SSH keys.
- our historical vignette will discuss danger of key reuse in WW2
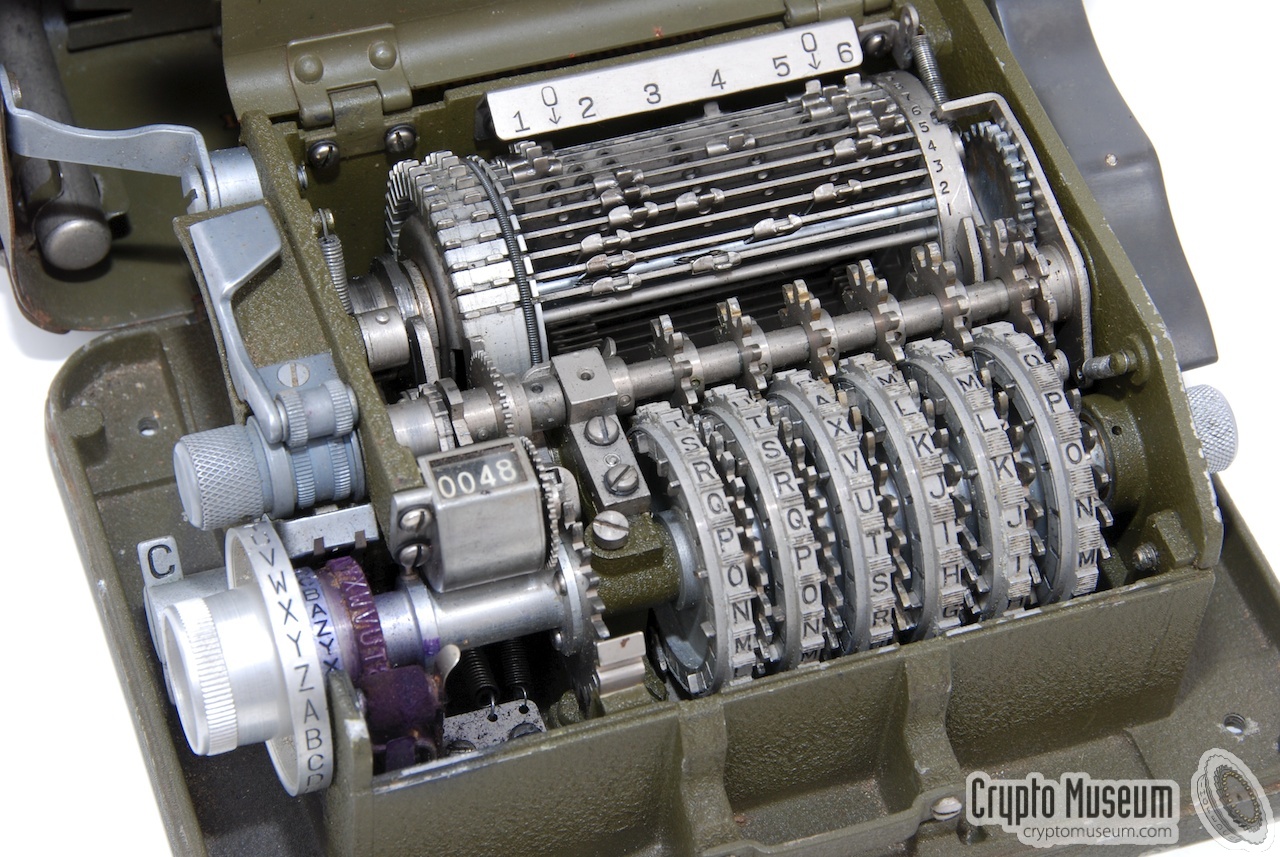
History Vignette - Pin&Lug Hagelin Cryptographs (C-3x/M209)
Bletchley Park Podcast
Bletchley
Park Podcast E131: It Happened Here: Secrets of the Supermarina
(91
min)
November 2021
Many visitors to Bletchley Park are familiar with the story of
breaking Enigma and reading German and even Japanese codes. But equally
important work was done on Italian ciphers.
Not only were the Code-breakers able to read Italian naval messages,
before and during the war, but this information was used to decisive
effect in the Battle for North Africa, and the ultimate defeat of Italy
in 1943. In this It Happened Here episode, Bletchley Park’s Research
Historian Dr David Kenyon reveals the secrets of one of Bletchley Park’s
lesser-known decryption successes.
As always, grateful thanks go to Dr Ben Thompson for voicing our
archival documents.
Featuring the following contributors from our Oral History
Archive:
Mavis Batey
Rozanne Colchester
Swedish Innovation, adopted by several countries
- Hagelin was protegé of Nobel
- Using adding-machine mechanical-calculating techniques to combine
key-wheels into additive key
- computes a different Caesar key at each position
- summing contributions from each rotor’s side-pin state, multiplied
by # lugs set opposite
- lugs move bars on a cage to make a temporary variable-toothed
gear
- which will advance the (reversed) cipher alphabet 0-27 places
“natural” position for clear letter
- before printing the enciphered letter.
- 1935 French requested Hagelin to adapt their desktop
Enigma-competitor (B-series)
- to a printing pocketable tactical (named C series)
- model C-35 & C-36 (1936) had 5 wheels (25 × 23 × 21 × 19 × 17,
different orders).
- Z prints as Space in Plain-text, as Z in Cipher-text.
- C-38 / M-209 / C38m : 6 wheels, added a 26-position wheel (still
mutually co-prime).
- M-209 / CSP 1500 (USA / USN) C-38 built under license by
Smith-Corona
- C38m Italian Navy, K prints as space (instead of Z).
Cracking Italian Navy HQ’s Hagelin C38m pinwheel in WW2
- Legend correction: BP crack of Afrika Korps supply convoys
- not ENIGMA ULTRA but Hagelin ZTI
- Italian SuperMarina = Navy HQ
- ZED like ULTRA but for RN
- HQ instructions for making up of convoys
- wrong cipher for task
- poorly used
- Weaknesses
- Depths
- Error / inexact re-transmission
- One very long message allows purely statistical attack
- (several medium long messages also)
How Broken
- Manual break of a depth
- Depths
- caused by errors
- subtract two aligned messages
- Cribs
PERK or
PERKSUPERMARINK`
- or codewords seen previously as covernames for ROMMEL, AFRIKACORPS,
TUNIS, etc
- complete-the-word cross-rif between 2 messages
- which discloses fragments of both messages and their shared key
- Infer settings from key disclosed in longest depth fragment
- internal: wheel pin positions and lug multipliers
- external: start position
- Read entire message, using Settings and analog hardware
- Use settings found to simplify break of other messages
Talent
Another Bill Tutte, Tommie Flowers & Dollis-Hill Gang at
P.O.R.S. legend that is not yet fully understood!
Bill Tutte of BP and the Dorris-Hill Gang for the
win, before their latterly-famous “Heath Robinson” and “COLOSSUS” attack
on Lorenz.
Tommie Flowers & Sidney Broadhurst of the Post
Office Research Station, London (aka Dollis-Hill) were better known in
the public for their post-war work on ERNIE1, the Post
Office’s Premium Bond Lottery randomizer; and in the
UNCLASS Electronics world (IEEE, ITU, etc) for the
electronic telephone exchange, 3 years before Bell’s comparable
1ESS was installed in NJ.
(scroll)
A NIGHTINGALE in the Post Office
NIGHTINGALE codename for a machine
- Built by Flowers & Broadhurst at PORS Dollis-Hill for BP
- to decipher Hagelin messages with a given key quicker than
mechanical
- and to crack monthly internal settings
- known to be used for Italian Naval HQ (Supermarin) Hagelin C38m
network
- may have been used for other Hagelin traffic?
“It is mostly unknown how it functioned.”
“An operator remembered it was like playing a church organ.”
(implies both a keyboard and a bank of toggle switches?)
(BP say they may have a photo unlabeled, that has repetition
of 6 units, which would be one per rotor, so plausible!)
NIGHTINGALE was the ^analog^ or emulator
for Hagelin (later CryptoAG) C38/C38m/M109/CSP 1500/AM-1.
Stepper Relays aka Uniselector
NIGHTINGALE was built with telecoms Stepper Relays aka Uniselectors,
Stepper switches, Steppers.
Steppers could be used as inside-out rotors, when rotors were used as
ROMs.
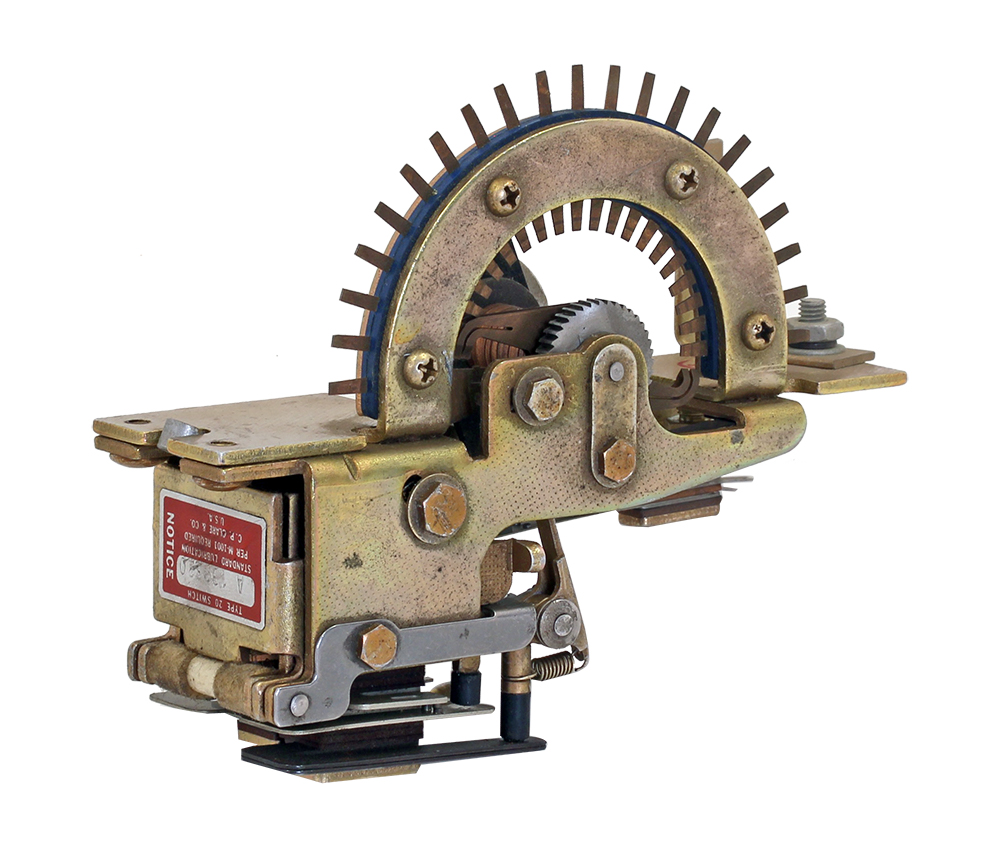

Uniselector Stepper Switches / Stepper Relays were ubiquitous in
pre-electronic electro-mechanical automated telephone exchanges (1927
how-to silent movie)
- IJ Diplomatic PURPLE or
System 97 Type B cipher machine used Stepper relays in lieu of rotors.
They were basically a semi-serial-, semi-parallel-access wired ROM.
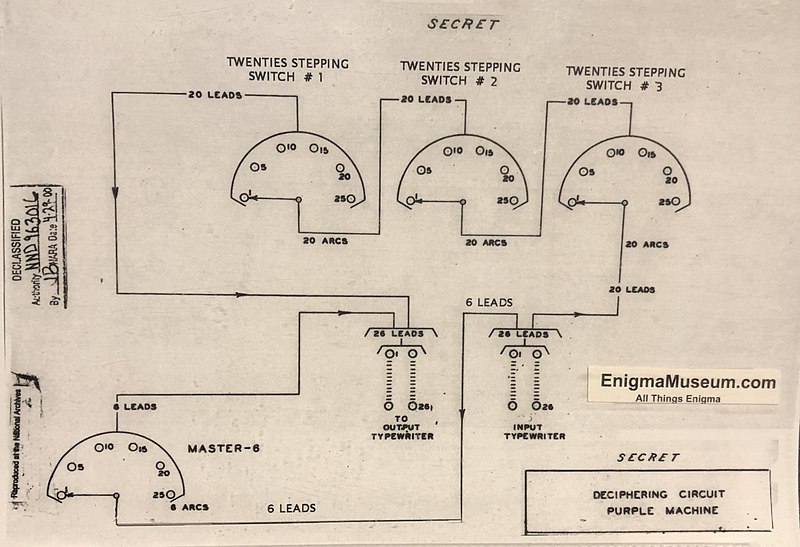 USA SIS
officer-mathematician
Leo Rosen recognized certain regularities in the cipher meant
stepper relays instead of physical rotors, so bought American 6p25t
steppers to recreate the machine!
USA SIS
officer-mathematician
Leo Rosen recognized certain regularities in the cipher meant
stepper relays instead of physical rotors, so bought American 6p25t
steppers to recreate the machine!
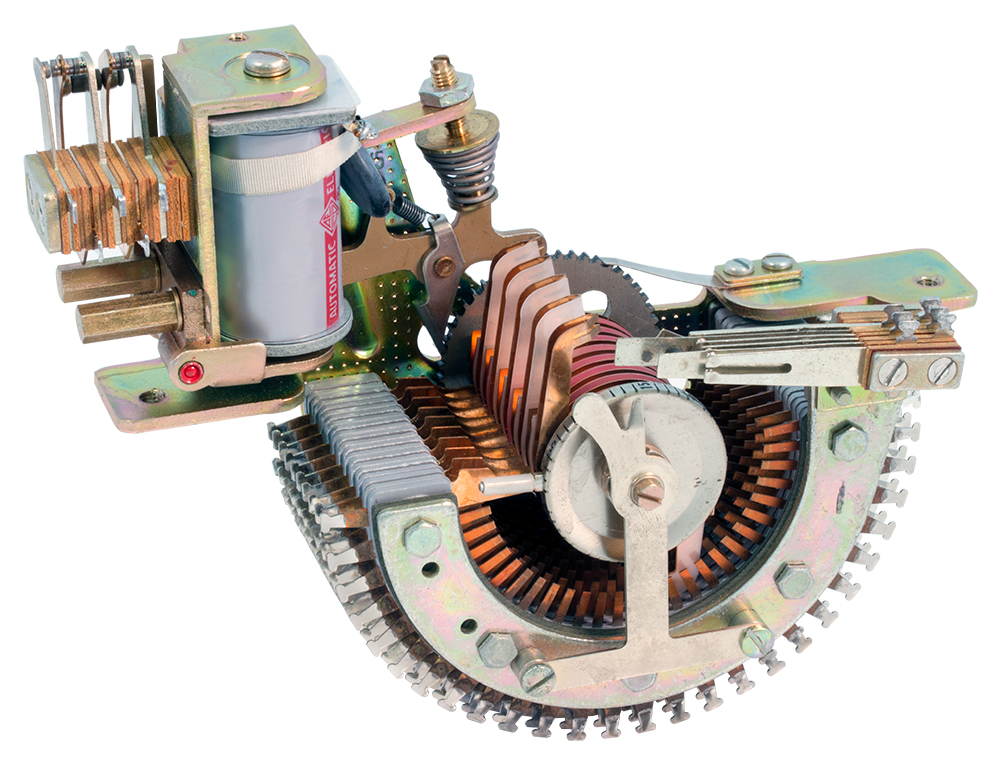
- UK PORS Dollis-Hill used Steppers in several “analyzers” for
GC&CS (BP) to make faster emulations of Enigma & Sturgeon and
presumably used them on the Hagelin NIGHTINGALE also. Might have used
26-throw to emulate 26 position rotors and 26-or-less pin-wheels
(different from PURPLE ROM method)?
- Uniselectors were also used in the slower portions of Dollis-Hill/BP
Colossus (TUNNY), and in the Lorenz/TUNNY emulator (for reading the rest
of a broken message).
- GPO Uniselectors were even used in the Enigma-solving Bombes, in the
“machine gun” circuit to test a “stop”’s validity, by running through
combinations quickly.










 USA SIS
USA SIS
