 ‘GPU Assisted Brute Force Cryptanalysis of GPRS, GSM,
RFID, and TETRA: Brute Force Cryptanalysis of KASUMI, SPECK, and
TEA3.’
‘GPU Assisted Brute Force Cryptanalysis of GPRS, GSM,
RFID, and TETRA: Brute Force Cryptanalysis of KASUMI, SPECK, and
TEA3.’Sept 17, 2025
“Abundance of Caution” is C-suite lingo for “Oopsie, oh flying squirrel”
In other news
Revocation of certs is a solution that creates more problems (centralized, DoS, …). The alternative is to discard certificates frequently. (This is more plausible for server certs than for email certs, where one would like to be able to decrypt a message when it’s relevant, not have to decrypt immediately upon receipt.) This also limits the window of vulnerability of TLS server cert and private key saved in publicly readable cloud backups / staging areas / GitHub repos / container repo; the private key expires 6 days after received; save a(n almost) stale key to the repo, discloses nothing, and autoupdates?
UK white paper Schneier & friends comments
Advanced := Beyond protecteding data at rest and data in motion; allowing some processing of protected data.
Their examples:
key takeaways are
Their gloss of their examples:
NIST SP 800-63 Digital Identity Guidelines includes passwords. This is officially only applicable to Federal information systems, but constitutes a best practice for the rest of us to be aware of.
Schneier on 2024 draft’s password rules
These are actual wireless communications protocols’ keys.
This research shows that some key-sizes are within brute-force now with state-actor scale (e.g. Top500) clusters of GPUs or hypothetical specialized hardware, and others may be in range by 2050.
Venona-level persistence-play is already in play1. Today’s cellphone intercepts may be cracked in the future. For the highest priority, investigators may be willing to dedicate a cluster for a year to get the session-key for a previously recorded conversation. And it will only get more affordable.
Updating our prior discussions (in 20192, 20213, and 20224):
Nice discussion by use-case by a cryptologist who finds vulns. By Use Case is important, as the flaws in PGP/GPG usage largely come from trying to be the one Swiss Army Knife to pound all nails.
Covers use-cases:
tl;dr:
But even with Signal secure group messages, OpSec requires you not add the wrong person from your Contacts!
Key notes from Schneier &friends comments
Also, reminder that Telegram doesn’t default to secure, and even when security is enabled, it’s only for 1-to-1 not group chats. Telegram is find
And as always YMMV, evaluate your threat-model.
♳ Reprises (♳) and updates last major PQC status update Sept 2022 which is excerpted below with recycled “♳ Review” markings.

Quantum Superposition when used for computing.
Such bits are in quantum superposition of True and False, which is a bug in classical computing but a feature in QC.
This allows non-deterministic algorithms.
Quantum Annealing - big qubit counts, great for optimization problems
but not cryptology. (?yet? well maybe …) Not general purpose.
Quantum Circuit/Logic - small numbers of qubits so far.
In theory, algorithms for these hardware types can use non-deterministic parallelism to evade classical performance limits, and in particular, could allow factoring fast enough to be dangerous, provided big enough quantum circuits can be made to work.
Yes !

Quantum Cryptanalysis
♳
Every unbreakable cipher has been broken eventually (at least partially5).
20thC RSA and other PKI not guaranteed proof against either of:
Schor’s Algorithm in theory would factor fast on enough quantum circuits but 21 is not a large number yet. (see also Wikipedia. Some say 433 bits on IBM Osprey QC is enough for RSA2048 with Schor’s algo needing 372 Qubits (with pre-processing and post-processing), but will it work? Schneier and Schor doubt it. Shouldn’t someone try it?)
Other probabilistic quantum algorithms (Grover, GEECM, Variational Quantum Factoring (VQF)) can do some much bigger numbers (which may just define new class of unsafe primes??), and with classical pre-processing, can use a much smaller number of qubits than the ^obvious^ log2N.
not clear this will ever be able to generally break RSA4096, but it’s not impossible, so prudent to plan for that day.
(Hype, not yet dangerous)
BBC: Google unveils ‘mind-boggling’ quantum computing chip
MSN: Google’s Willow quantum chip breakthrough is hidden behind a questionable benchmark
See caveats on Wikipedia 6:
Per Google company’s claim, Willow is the first chip to achieve below threshold quantum error correction.[1][2] However, a number of critics have pointed out several limitations:
(quoted at length in notes)
Wikipedia Willow_processor, #Criticism, 2025-08-08 continuing:
The logical error rates reported (around 0.14% per cycle) remain orders of magnitude above the 10^6 levels believed necessary for running meaningful, large-scale quantum algorithms.[9] To date, demonstrations have been limited to quantum memory and the preservation of logical qubits’without yet showing below’threshold performance of logical gate operations required for universal fault’tolerant computation.[10] Media coverage has been accused of overstating Willow’s practical significance; although error suppression scales exponentially with qubit count, no large’scale quantum algorithms or commercial applications have yet been demonstrated on Willow.[11] Observers caution that achieving below’threshold error correction is only one milestone on the path to practical quantum computing’further hardware improvements (lower physical error rates) and vastly larger qubit arrays will be required before industrially relevant problem’solving is possible.[12] Some experts note that Willow remains a research prototype within the Noisy intermediate-scale quantum era, still far from delivering the practical, fault’tolerant performance required for real’world applications.[13]
♳ * Classical “Forward Secrecy” property requires tha old messages not broken by later loss/compromise of host key
Generalized: old saved messages not broken by later breakthroughs either.
Realistic threat? 
* VENONA: It worked Once! ^[see BLU Sept 2018 footnote above]
* We now have a Vacuum Cleaner of Holding (_Greenpeace photo c/o Wikimedia_)So yes, it can happen again.
Normal Forward Secrecy requires that if e.g. the Host Key is compromised later, any retained cryptograms sent with nonce keys negotiated with the compromised Host Key aren’t also compromised.
This is nice, but we’d also like to protect against advances of technology, e.g. fast factoring or solutions of discrete logs or even massively parallel brute-force key-search on Top500 scale GPU clusters8.
This may not be within your threat model, yet, but in dystopian plausible futures, things you’ve already discussed/downloaded might be retroactively illegal/disloyal and oops.
♳
The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks. – NIST
♳
National Institute of Standards & Technology started a multi-round competition, similar to with AES and SHA3 competitions
NIST, the Bureaucracy formerly known as NBS.
Goal is to have PQC ready for use not only before quantum breakthrough but early enough (roughly now) that anyone who wishes to avoid save-intercepts-now-to-break later can switch quickly; although it may already be too late WRTO NSA archive?
This competition was “more brutal” than prior; of 69 candidates, peer cryptanalysis has broken 62. So far.
♳
RSA2048 in play or not? - Chinese academic paper claiming 2k bit RSA within range of current gen NON-fault-tolerant QC, no great surprise given Qubits available and theoretical algorithm size. Schor and Schneier unconvinced - does it actually converge w/o FT? Schneier 2023-01

[2023.02.28] CRYSTALS-Kyber is one of the public-key algorithms currently recommended by NIST as part of its post-quantum cryptography standardization process. Researchers have just published a side-channel attack’using power consumption’against an implementation of the algorithm that was supposed to be resistant against that sort of attack. The algorithm is not ‘broken’ or ‘cracked’’despite headlines to the contrary’this is just a side-channel attack. What makes this work really interesting is that the researchers used a machine-learning model to train the system to exploit the side channel.
OTOH as seen in TETRA:BURST, a side-channel attack can be used to extract key or algorithm from a piece of equipment that falls into opponent lab.
♳
TL;DR No. It’s happened. (see in notes)
Lack of randomness failure isn’t just hypothetical, lots of SSH keys got invalidated in 2008 because they were well-known-primes.
random^[DSA-1571-1 openssl predictable random
number generator {CVE-2008-0166}
{Schneier}
which compromised many SSH keys.(WTAF? Yep. Debian packagers applying normal
best practices where they shouldn’t even touch (Normal doesn’t
apply!) had removed the entropy-harvesting because Valgrind and
Purify gave accessing uninitialized memory warnings. Well
yeah, that’s how we harvest entropy! Another problem (mostly
solved?) is host key generation at VM start - the VM’s entropy is rather
deterministic (biased) at that point. Similarly, optimizing compilers
removing zeroing memory prior to releasing it can allow keys to leak
into the memory pool. Cryptographic software is an ongoing a battle
against computer ^science^ that ^knows better^.)
And failure to salt wouldn’t surprise me when non-specialists (applications developers, database programmers, protocol developers) who should stick to packaged PKI use-case libraries (e.g. NaCl) try to use cryptographic primitive routines directly to avoid dependencies.)
2023 added few more low-entropy initialization examples added to the list.
And 2024’s PuTTY key disclosure was due to implementing low-entropy nonces badly for use in VMs and everywhere else.
Won’t someone think of the random numbers?
FIPS Allowed: NIST announced
finalized PQC standards for 3 of 4 “winners” (3 more to come)
FIPS Approved.A year ago, NIST finalized 3 FIPS PQC standards and selection of several PQC algorithms (1 KEM, 2 DSA). Since then, a few more have progressed through the process.
“Securely” presumably is regarding timing.
Cryptographic math wants to be not only one-way functions but (in a world where encryption is often on a shared CPU) not only fixed time but also fixed tempo, to avoid side-channel (power, CPU%, memory access pattern, …) disclosure of key bits or key correlatives.
NIST SP 800-90A PRE-DRAFT Call for Comments: Recommendation for Random Number Generation Using Deterministic Random Bit Generators
c/o 🐘
Dec. 2024: NIST proposed a 256-bit block variant of AES with a static 256-bit key size.
Public comments were open until January 25, 2025.
Schneier; Fed.Reg. ; NIST PR el Reg; CloudFlare NIST March IR Digicert re FN-DSA status; NIST HQC
The Battle of Midway was won miles away, weeks before, in a bunker in Hawaii. ⎄
Battle of Midway wasn’t a surprise landing after-all.
In the spring of 1942, Japanese intercepts began to make referencesto a pending operation in which the objective was designated as “AF.” Rochefort and Captain Edwin Layton, Nimitz’s Fleet Intelligence Officer, believed “AF” might be Midway since they had seen “A” designators assigned to locations in the Hawaiian Islands. Based on the informationavailable, logic dictated that Midway would be the most probable place for the Japanese Navy to make its next move. Nimitz however, could not rely on educated guesses. In an effort to alleviate any doubt, in mid-May the commandingofficer of the Midway installation was instructed to send a messagein the clear indicating that the installation’s water distillationplant had suffered serious damage and that fresh water was neededimmediately. Shortly after the transmission, an intercepted Japaneseintelligence report indicated that “AF is short of water.” Armed with this information, Nimitz began to draw up plans to move his carriers …
Even before the Coral Sea engagement, based on what he was decoding, Rochefort predicted a major Japanese attack in the Central Pacific. On May 12, the American decoders discovered that the letters ‘AF’ symbolized the Japanese code name for their target. By May 25th, Rochefort and Captain Edwin Layton, Admiral Chester Nimitz’s Fleet Intelligence Officer, were convinced that ‘AF’ stood for Midway Island. Rochefort had even pinpointed the date of the Japanese attack–June 4, 1942 and that a diversionary attack would take place somewhere in or around Alaska around June 3. There was just one problem: Rochefort had to convince the Washington ‘planners’ who would not believe that Midway could possibly be the target that they were wrong. Commander Jasper Holmes, Rochefort’s assistant, devised a plan to prove that ‘AF’ was indeed Midway, a plan to which Admiral Chester Nimitz agreed. Nimitz instructed Midway to send a clear text message that falsely reported the island was low on fresh water. The Japanese obligingly intercepted the message and promptly and dutifully reported that ‘AF’ was low on fresh water. That was the proof Nimitz needed; he could take action.
(It was the Flag-officer variant that Rochefort’s Station HYPO had been dedicated to prior to Dec 7, 1941. They joined the other stations working on general fleet JN-25b by Dec 25th.)
Only after Pearl Harbor attack was Station HYPO, Navy Cryptological unit there, assigned to the suddenly higher priority “JN-25b” IJN operational code.
recovering a new key fairly easy if codebook already mostly solved and common message patterns known
recovering additional codegroup meanings somewhat challenging linguistic problem if additive key solved
when both change, need to collect volume for depths and re-enter using known common messages.
Failure to use Russian Copula, discourage routine patterns allows retaining contact!
Rochefort’s War e.g. p.206
Breaking JN-25(b) would be like peeling back the layers of an onion; layer after layer would have to be sliced away and pulled apart before the code inside was revealed. Each code group was disguised by yet another five-digit group of a possible 50,000 random numbers, called additives, contained in a 300-page volume. Called the additive book, this consisted of many pages of five-numeral groups, each available to disguise a code group.
See also discusion of Musicians recruited into Rochefort’s Station HYPO; NSA and Wikipedia bios of Rochefort and Chicago fracas Web pages.
 Using IBM
405 Tabulators
Using IBM
405 Tabulators
Keypunch leading 16 × 5 figure groups per 80 column cards
Search for coincidences, and common differences
also for common prefixes of message
statistical tests; common adjacencies; index of differences seen.
also cards for known placode groups’ Kana (and translation?) to produce (partial) decrypts
Encicode : — portmanteau of enciphered code, the numeric or alphabetic codegroup as protected by a superencipherement. (Coined by WFF himself!) See
for historical reasons, Pearl Harbor HYPO had dedicated IBM tabulators in the bunker (SCIF) and space to add crew
Rochefort’s War p.39 > This involved a second book consisting of thousands of additional numerals, called additives. A code clerk on the sending end would simply superimpose a set of randomly chosen numerals on the code groups. Another code clerk on the receiving end looked for a keyword in the message that told him what page to turn to in the additive book to find how the code had been enciphered, thereby enabling him to strip off the additives before looking up
the codegroup and its meaning were punched on an I.B.M. card and stored in the machine. When an intercept came in, a clerk would punch its codegroups on I.B.M. cards and feed them in. The machine automatically made the run of repeated subtractions and the check of its mechanized difference ‘books’’ necessary to find the identical remainders, and then, with human guidance, the runs to reconstruct the relative additive sequence, correct it to the absolute sequence, and strip it from the encicode message. The machine would then compare the placode groups with the decode cards in its storage and print out the plaintext for whatever decode cards it had. Presumably it would also print out the various possibilities in the case of garbled or partial codegroups. It could also make frequency counts and contact counts and on command could disgorge a desired set of statistics’all codegroups preceding and following a given codegroup, for example.
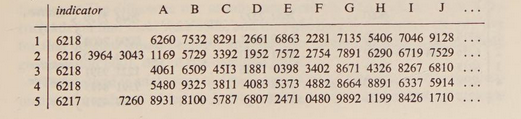 5 messages in depth
5 messages in depth
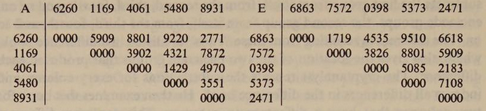 Difference runs on columns A and E.
Difference runs on columns A and E.
8801 and
5909 are common differences between
columns A and E.Technique to strip additive with offline tabulators was discovered by at least one German agency as well.
It is generally called the ‘difference method.’ The cryptanalyst first identifies, by indicators or traffic analyses or other information, a group of encicode messages that he believes used the same basic code and portions, at least, of the same long additive key. Using repetitions or clues from indicators as anchor points, he places the messages one under another so that the identical portions of the additive key will stand in vertical alignment. ’
He subtracts every encicode group in a column from every other. He subtracts the first group from itself, from the second, third, fourth, and so on, encicode groups, the second group from itself, from the third, fourth, and so on. The differences resulting from these ‘runs’ are listed in a difference book, which also gives the location of the two encicode groups that produced each difference. The cryptanalyst repeats the subtractions for every column and indexes all differences in the difference book. He then examines this book for two columns that have a difference in common. This common difference indicates that the two columns include the same placode group, which each column has enciphered with its own additive.
Recovery of code-group meanings was called ‘book-breaking’. Removal of additive key was called ‘stripping’, and the ladies and gentlemen who did this were called ‘strippers’.
Example from Hinsley & Stripp:

Works like an N-dimensional Cross-word puzzle … but with cells being codewords representing words or phrases, and connections being same-offsets in codeword sequence.
Hinsley&Stripp p.297..299
> Message No. 1 is inscrutable. No. 2 is clearly a routine report of
stocks held. No. 3 offers no help yet. If we try ‘large bombs’ for the
first missing key-group in Message No. 2, the key needed to produce it
gives ‘our’ in No. 1, and ‘advance’ in No. 3. We are in business. But we
are unlikely to spend hours going through all possible numerals to
continue No. 2 unless there is a very special reason. > To cut a long
story short: for the second missing key-group, ‘towards’ in No. 3 gives
‘troops’ in No. 1, and ‘545’ in No. 2. For the third, ‘incendiary bombs’
in No. 2 gives ‘were forced to’ in No. 1, and ‘Mandalay’ in No. 3. The
fourth is harder: the obvious guess ‘abandon’ (or a synonym) for No. 1
produces nonsense, but if we assume that one digit has been garbled in
reciphering, transmission, or interception’a common phenomenon’it works,
giving ‘2250’ in No. 2 and ‘intending’ in No. 3. Finally,
‘delayed-action bombs’ in No. 2 gives ‘TI’ in No. 1 and ‘to cross’ in
No. 3. The sense is clear in Messages No. 2 and No. 3. …
(See link above for the rest of the narrative.)
Another worked example of Kerckhoff’s method applied to letter-wise ciphers in depth is in Barker.
The YouTube of this presentation will be linked on BLU.org along with these slides and extended notes etc as 2025-sep as per usual.
Prior
talks in this series - most talks have slides &/or
YouTube attached, sometimes extras.
Alas the YouTube audio pre-pandemic wasn’t great, BLU will need a
donation of a wireless clip-on mike if we ever return to
Hybrid/In-Person meetings. Or we all need to wear a wired or BT headset
while presenting in person?
News and Focus sections have embedded links.
Good security news streams to either research history or to follow
year round are Scneier
Crypto-gram and SANS ISC, the
latter being less cryptologic and more operational in focus – but both
cover the wide span of vulnerabilities, tools, remediations, etc, not
just the cryptologic that I’m cherry-picking here.
Highly recommended.
Start your day with the 5 minute SANS Internet Storm Center
StormCast pod-cast; the Red Team is, so, so should you.

references: Kahn and others in bibliography.
My 2018 vignette on VENONA OTP touched on book-breaking as well.
‘IA’ indicates available at Internet Archive.
Text provides a hands-on problem: an enciphered code problem with text in English that duplicates an actual Italian system used in Libya in 1940. The student is shown how to solve the problem with the concept of “differences” as applied to the analysis of an additive system being discussed in detail, and shown the use of “difference tables,” etc.
 Carlson, Elliot; Joe
Rochefort’s war : the odyssey of the codebreaker who outwitted Yamamoto
at Midway; 2013; Naval Institute Press.
Carlson, Elliot; Joe
Rochefort’s war : the odyssey of the codebreaker who outwitted Yamamoto
at Midway; 2013; Naval Institute Press.
Abstract Working from the basement of US Pacific Fleet Headquarters in Pearl Harbor from 1941, a small team of navy cryptanalysts and linguists known as the Combat Intelligence Unit (CIU) provided the US Pacific Fleet Command with timely details of the capabilities and intentions of the Japanese Imperial Navy (IJN) in the Pacific. A substantial portion of the CIU was comprised of 20 enlisted musicians of US Navy Unit Band 16, the band of the USS California (BB-44), who survived the sinking of their ship in the attack of December 7, 1941. The musicians were recruited to Combat Intelligence, retrained to perform tasks related to the deciphering of Japanese Naval Code JN-25b, and contributed to that unit’s celebrated intelligence successes of 1942. As the war waged on, several musicians from Band 16 transferred to the Naval Communications Complex at Nebraska Avenue in Washington DC, and three eventually joined the National Security Agency (NSA) and served through the height of the Cold War.
New details of alarming WWII press leak. The Chicago Tribune printed the big secret. Fortunately, the Japanese apparently didn’t read the Tribune.
The Washington Post has featured Naval Institute Press author, Elliot Carlson and the story behind his forthcoming book: STANLEY JOHNSTON’S WAR: THE REPORTER WHO SPILLED THE SECRET BEHIND THE U.S. NAVY’S VICTORY AT MIDWAY.
text
see the ♳ Review: Forward Secrecy slide in 2, and BLU 2018 footnotes below↩︎
2019 what to use, initial suggestions by use-case;↩︎
2021 what to use, 2019♳ with added caveat Keybase sold to Zoom;↩︎
2022 what to use, 2019♳ with a governmental PGP use failure;↩︎
See our prior discussions of GEE, VENONA for breaks of One Time Pad, e.g. 20182↩︎
see BLU Sept 2018 Venona footnote above↩︎
2025 1 Attacks only get better above↩︎