Cryptology Annual News Update and Vignette
Bill Ricker
for BLU.org
Sept 17, 2025
- Cryptology News Bulletins
- Post Quantum Cryptograpy update
- Historic Vignette
- Bibliography
1 Cryptology News Bulletins 2024-09 to 2025-09
“Abundance of Caution” is C-suite lingo for
“Oopsie, oh flying squirrel”
Let’s Encrypt: short-lived certificates &c
- LetsEncrypt
Dec. editorial announced automatically renewable 6-day server TLS
certificates, using the same automation used for the free 90-day certs.
In other news
- Now issuing IP
Address certificates,
- Turned off
- announced phased
shutdown of RFC 6962 Certificate Transparency Logs (in favor of
Static Certificate Transparency API);
timed to allow browsers to catch up.
UK NCSC advice on ‘Advanced Cryptography’
UK
white paper Schneier
& friends comments
Advanced := Beyond protecteding
data at rest and data in motion;
allowing some processing of protected data.
Their examples:
- Homomorphic encryption
- Private information retrieval
- Multiparty computation
- Zero-knowledge proofs
- Private set intersection revealing your whole list
- Attribute-based encryption attributes
key takeaways are
- Don’t roll your own security code (per usual)
- these techniques are immature so get best help
Notes on Advanced Cryptography
Their gloss of their examples:
- Homomorphic encryption:
performing calculations directly on encrypted data
- Private information retrieval:
conducting a query into a database, without revealing the query to the
owner of the database
- Multiparty computation:
carrying out a calculation cooperatively, but without sharing secret
inputs
- Zero-knowledge proofs:
proving the possession of some secret knowledge without revealing
it
- Private set intersection:
learning which data items you have in common with someone else, without
revealing your whole list
- Attribute-based encryption:
limiting decryption of messages to anyone possessing a specific set of
attributes
What to use instead of PGP, FB IM, …
Updating our prior discussions (in 2019, 2021, and 2022):
Nice discussion by use-case by a cryptologist who finds
vulns. By Use Case is important, as the flaws in PGP/GPG usage
largely come from trying to be the one Swiss Army Knife to pound all
nails.
tl;dr:
- SecureDrop
- Signal
- Whistle blower support services
But even with Signal secure group messages, OpSec requires you not
add the wrong person from your Contacts!
2 What’s up with Post Quantum Cryptography?
Review: What’s Quantum Computing?
♳ Reprises (♳) and updates last major PQC status update Sept
2022 which is excerpted below with recycled “♳ Review” markings.

Quantum
Superposition when used for computing.
- QC measured in “qubits” not bits
- 30% True, 70% False.
♳ Review: Kinds of Quantum
Hardware
♳ Review: We’re discussing
PQC before QC?
Yes !

Review: What’s the problem?
♳
- Unbreakable ciphers aren’t always unbreakable, for always.
- QC could theoretically break most PKI
- Schor’s Algorithm / Grover’s / VQF
- discrete log as well as prime factoring, even elliptic curves
- 2024-01-05 Improving
Shor’s Algorithm
Review: Generalization of Forward Secrecy
♳ * Classical “Forward Secrecy” property requires tha old messages
not broken by later loss/compromise of host key
Review: NIST Post-Quantum Cryptography Standards
♳
The goal of post-quantum cryptography (also called quantum-resistant
cryptography) is to develop cryptographic systems that are secure
against both quantum and classical computers, and can interoperate with
existing communications protocols and networks. –
NIST
Review: NIST PQC Competition
♳
National Institute of Standards & Technology started a
multi-round competition, similar to with AES and SHA3 competitions
Review: Quantum Cracking 2023
♳

[2023.02.28] CRYSTALS-Kyber is one of the public-key algorithms
currently recommended by NIST as part of its post-quantum cryptography
standardization process. Researchers have just published a side-channel
attack’using power consumption’against an implementation of the
algorithm that was supposed to be resistant against that sort of attack.
The algorithm is not ‘broken’ or ‘cracked’’despite headlines to the
contrary’this is just a side-channel attack. What makes this work really
interesting is that the researchers used a machine-learning model to
train the system to exploit the side channel.
OTOH as seen in TETRA:BURST, a side-channel attack can be used to
extract key or algorithm from a piece of equipment that falls into
opponent lab.
Review: Known weaknesses
♳
- breaks eliminated 62 of 69 entrants in Rounds 1 to 4
- including the two front-runners, Rainbow and SIKE
- 7 remain, will they survive?
- FALCON would be compromised by a lack-of-randomness in salt, or
failure to salt, as repeating same key and hash again gives too much
information.
TL;DR No. It’s happened. (see in
notes)
NIST PQC Timeline (updated)
- 2022-04-28 How
to Prepare Your PKI for Quantum Computing (April 28, 2022)
- 2023-03-03 Post-Quantum
Cryptography Conference (Friday March 3, 2023 - Ottawa, Canada)
- 2023-08 FRN
RFC Draft Standards FIPS 203, 204, 205.
- 2024-04 Fifth PQC Standardization Conference
- 2024-08-15 FIPS Standards;
FIPS Allowed: NIST announced
finalized PQC standards for 3 of 4 “winners” (3 more to come)
- FIPS 203:
Module-Lattice-Based Key-Encapsulation Mechanism Standard (ML-KEM)
- proposed as “CRYSTALS-Kyber”
- general encryption (payload symmetric key encapsulation), for data
in motion
- August 2024
- FIPS 204:
Module-Lattice-Based Digital Signature Standard (ML-DSA)
- proposed as “CRYSTALS-Dilithium”
- Digital Signatures, authentication
- August 2024
- FIPS 205:
Stateless Hash-Based Digital Signature Standard (ML-DSS; SLH-DSA)
- proposed as Spincs+
- Digital Signatures, authentication
- August 2024
- 2024-10-24 PQDSS Round 2 starts
- 2025-03-11 future FIPS 207 HQC-KEM selected from PQKEM round 4.
- 2025-08-28 FIPS 206 Draft (FN-DSA) submitted
- ….. you are here …..
- 2025-09-24 ’ Sixth PQC Standardization Conference the week after
this annual talk, so expect more news soon! Conference
page has Agenda; already has 2 sessions on Cryptanlysis of PQDSS
Round 2.
- 2025/26 FIPS certification for the PQC algorithms;
FIPS Approved.
- …. and eventually, FIPS disapproval/phase-out/banishment of non-PQC
legacy algorithms …
NIST
PQC
2025 NIST PQC FIPS 206 FN-DSA draft
A year ago, NIST finalized 3 FIPS PQC standards and selection of
several PQC algorithms (1 KEM, 2 DSA). Since then, a few more have
progressed through the process.
- FIPS 206 draft submitted Falcon / FN-DSA
- FN-DSA (Falcon, also DSA) was scheduled for finalization later in
2024 but has only just been submitted as draft standard August,
2025
> Nov 7, 2024 Falcon (to be renamed FN-DSA) seems much better than
SLH-DSA and ML-DSA if you look only at the numbers in the table. There
is a catch though. For fast signing, Falcon requires fast floating-point
arithmetic, which turns out to be difficult to implement securely. CloudFlare
“Securely” presumably is regarding timing.
Cryptographic math wants to be not only one-way functions but (in a
world where encryption is often on a shared CPU) not only fixed time but
also fixed tempo, to avoid side-channel (power, CPU%, memory access
pattern, …) disclosure of key bits or key correlatives.
2024-OCT NIST PQC DSA Round 2
- Round 2 DSA candidates, October 2024: 14 new candidates (looking for
diversity) ♳
- CROSS Codes and Restricted Objects Signature Scheme
- LESS Linear Equivalence Signature Scheme
- SQIsign
- HAWK
- Mirath (MIRA+MiRitH)
- MQOM MQ on my Mind
- PERK
- RYDE
- SDitH Syndrome Decoding in the Head
- MAYO
- QR-UOV
- SNOVA
- UOV Unbalanced Oil and Vinegar
- FAEST
2025 future FIPS-207 selected Hamming Quasi-Cyclic (HQC, KEM)
- selected from fourth round candidates
- “backup for ML-KEM”, “different math”
- Key-Encapsulation Mechanism (KEM), for data in motion
- selected March 2025; targetting draft standard 2026, final FIPS
2027
- this selection sidelines the other fourth-round contenders BIKE
(close), Classic McEliece (deferred pending ISO; huge keys), SIKE
(broken).
- HQC had the simplest hardness assumptions.
3 History Vignette - Midway is low on water
The Battle of Midway was won miles away, weeks before, in a bunker in
Hawaii. ⎄
Historic Context
Battle of Midway wasn’t a surprise landing after-all.
- Spring 1942, months after Pearl Harbor
- Decodes show IJN planning next offensive against “AF”
- various two-letter codes AH, AK, … were Hawaiin islands
- AF should be nearby if consistent
- inferred must be Midway Is., but not conclusive
- strategem to prove it: feed a Known Plain Text to IJN listeners and
hope they send it in code being read
- Midway sends LOW ON WATER in the clear (as if not considered
secret)
- IJN sends AF LOW ON WATER in JN-25b, intercepted &
decrypted.
- USN carriers ambush IJN carriers
Revenge of Pearl Harbor Navy
Only after Pearl Harbor attack was Station HYPO, Navy Cryptological
unit there, assigned to the suddenly higher priority “JN-25b” IJN
operational code.
- 3rd edition codebook per IJN records, but version “b” in USN
records
- 5 digit code-words (code-groups) per word or phrase encoded
- superenciphered by additive key
- codebook versions reissued periodically
- key table booklets (of 50,000 5-digit random nubmers) reissued more
often
- Some progress already made by other stations
Processing Encicode to find, strip Additive key
 Using IBM
405 Tabulators
Using IBM
405 Tabulators- Keypunch leading 16 × 5 figure groups per 80 column cards
- Search for coincidences, and common differences
- also for common prefixes of message
- statistical tests; common adjacencies; index of differences
seen.
- also cards for known placode groups’ Kana (and translation?) to
produce (partial) decrypts
Method of Differences
- Calculate (and index and record!) the differences
of all the encicode groups in a message.
- Using Indicator or Kappa/Chi tests, align messages using common key
in depth
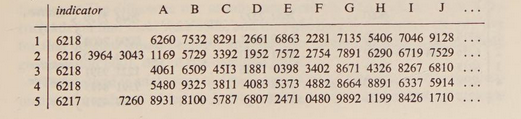 5 messages in depth
5 messages in depth
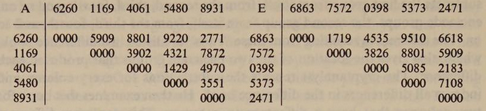 Difference runs on columns A and E.
Difference runs on columns A and E.
- note
8801 and
5909 are common differences between
columns A and E.
- (full differences would show more such)
- subtracting relative difference from all of the column produces
relative key and relative placode groups.
Book-Breaking
- Can follow stripping, or can lead stripping.
- first: recover code-groups for stereotyped beginning and end of
message
- second: code-groups used for numerals and spelling non-coded-words
broken as simple cipher
- already known groups plus context of message (from, to, when,
length, military situation) suggest values for first group in a gap
- if a One Part Code, the code and plain-text values are in
numeric=alphabetic order, so adjacency is a big hint
- cross-riff messages in depth
- which may solve gaps in Additive key-book as well
- assuming a group in a gap from context implies a difference, which
will imply code-groups for messages in depth; do they make all sense
too?
Using a Depth
Example from Hinsley & Stripp:

Stripp-298-depth
Works like an N-dimensional Cross-word puzzle … but with cells being
codewords representing words or phrases, and connections being
same-offsets in codeword sequence.
My talks
The YouTube of this presentation will be linked on
BLU.org along with these slides and
extended notes etc as 2025-sep as per
usual.
Prior
talks in this series - most talks have slides &/or
YouTube attached, sometimes extras.
Alas the YouTube audio pre-pandemic wasn’t great, BLU will need a
donation of a wireless clip-on mike if we ever return to
Hybrid/In-Person meetings. Or we all need to wear a wired or BT headset
while presenting in person?
News + Focus
News and Focus sections have
embedded links.
Good security news streams to either research history or to follow
year round are Scneier
Crypto-gram and SANS ISC, the
latter being less cryptologic and more operational in focus – but both
cover the wide span of vulnerabilities, tools, remediations, etc, not
just the cryptologic that I’m cherry-picking here.
Highly recommended.
Start your day with the 5 minute SANS Internet Storm Center
StormCast pod-cast; the Red Team is, so, so should you.
Cryptologic History – general references
Cryptologic History – 2025 – Glossary
- additive — numerical superenchipherment key, added
to book numeric code group (added without carry)
- additive book = key-table
- cipher - cryptographic protection of text via operations on the text
(typically characters) rather than semantic units (words); substitution
and transposition are the classical categories.
- code — cryptographic replacement of semantic units, whole words and
phrases, with words or (typically fixed size) sequence letters or
digits. Hence “four digit code”, “five digit code”, “five letter
code”.
- depth — several messages sent in same time-span of a key, which must
be aligned, which can be used to solve each message relative to the
others.
- encicode — portmanteau of enciphered code, the numeric
or alphabetic codegroup as protected by a superencipherement.
- indicator — a group inserted into a message that looks like
an encicode group but actually indicates the
offset into a “large”? table of key groups where the
message additive starts. ?(“large” for manual
encipherment turns out to be small for automated processing on IBM
Hollerith Tabulators, let alone modern computers.)
- key(s) — secret value(s) used with a method to encipher and
decipher. In superenciphered code, the
key is typically an additive, a sequence of one,
several, or very many nonsense numeric groups.
- key book, key table —in WW2 codes, periodical secret booklet of
several thousand numerical codegroups to be used as
additive key for it’s period of validity (one to three
months). See indicator. The replacement key-book must
be distributed to all stations before cut-over, else some messages may
be sent in both old and new key which is a compromise if noticed (same
length same day from same station is a major “tell”!)
- key-breaking — wrto book-codes, the hard phase of
key-stripping. (Can also be used wrto recovering
day-key of rotor systems, where “setting” “wheel breaking” are specific
forms.)
- key-stripping — reduction of intercepted encicode
to relative or absolute placode groups. If current
key-book (mostly) already recovered, indicator may
allow direct mechanical stripping (on IBM Hollerith Tabulators); if not,
requires aligning in depth and differencing to find
common differences.
- placode — portmanteau of plain code, the numeric or
alphabetic code group listed in the codebook, distinguished from
encicode.
- subtractive — UK usage for additive key (because cryptanalysis
required subtracting the additive added in encipherement)
- superencipherment — protection of code-groups of a Code proper.
Typically via an additive key, but transposition or
combination of transposition and substitution also historically used.
The placode is the unprotected codegroup(s), and the
encicode is the protected codegroup(s).
- superimposition = depth
references: Kahn and others in bibliography.
Cryptologic History – 2025 – topic-specific
My 2018 vignette on VENONA OTP touched on
book-breaking as well.
🕮 books & 📑 whitepapers
‘IA’ indicates available at Internet
Archive.
- 🕮 Barker, Wayne G.; Cryptanalysis of an
enciphered code problem : where an “additive” method of encipherment has
been used; 1979; Laguna Hills, Calif. : Aegean Park Press;
- IA
Text provides a hands-on problem: an enciphered code problem with
text in English that duplicates an actual Italian system used in Libya
in 1940. The student is shown how to solve the problem with the concept
of “differences” as applied to the analysis of an additive system being
discussed in detail, and shown the use of “difference tables,” etc.
- 🕮
 Carlson, Elliot; Joe
Rochefort’s war : the odyssey of the codebreaker who outwitted Yamamoto
at Midway; 2013; Naval Institute Press.
Carlson, Elliot; Joe
Rochefort’s war : the odyssey of the codebreaker who outwitted Yamamoto
at Midway; 2013; Naval Institute Press.
- Thank you to Federico Lucifredi who gifted me a
copy of this book!
- The book on Station Hypo, JN-25b, and Midway.
- IA
Borrow
- Appendix 1: “Rochefort’s DSM Citation” p.457
- Appendix 2: “Breaking JN-25(b)” pp.458-460; has (created) example
message
- Appendix 3: “The Meaning of Midway” p.461ff.
- Appendix 4. “The Kido Butai and Radio Silence”
p.465ff.
[Kidō
Butai = 機動部隊, “Mobile Strike Force” = the collection of the
IJN Fleet Carriers supporting the First Air Fleet (第一航空艦隊,
Daiichi Kōkū Kantai) of the Imperial Japanese Navy, and by
implication, upto five Divisions (pairs) of Aircraft Carriers plus
supporting capital, escort, and support vessels; 3 Divisions or 6
Carriers in the Pearl Harbor mobile strike task force.]
- pp. 39, 206, 207 cited; much more useful background.
- Glossary pp. 539-541
- 📑 Donovan & Mack, Annotated
Bibliography on Cryptography in Australia in WW2; Peter
Donovan, John Mack. Includes excerpts; esp. re F.H.Hinsley, p.10, and
Huh Melinsky, p.15. See also USydney+UNSW WW2 Codes
project homepage and linked popular-press article.
- 🕮 Hinsley & Stripp, Codebreakers:
the inside story of Bletchley Park IA
Borrow 1, 2
- p.297
ff has example of breaking a new stretch of additive
- breaking a new key-table requires depth and mostly good code-book
recovery (and any subsidiary re-cipher), or known-plaintext &/or
cribs.
- Part 5 Japanese Codes §26-30 pp.255-305.
- adders (US) = subtractors (UK)
- Italian naval book-breaking pp.61-63
- p.279, “book breaking”; JN-25 variants.
- 🕮 Kahn, D.; The
Codebreakers, 1967-1968, 1997 (rev).
Kerckhoffs, La Cryptographie
Militaire (Paris: Baudoin, 1883 and later reprints). (Fr.) 🕮
(Fr.)
📑 1st appearance in journal; (En.)
📑 (Trans. for American Cryptogram Assoc., 1964).
- p.31f
shows solving mixed alphabet with repeating key with several messages in
depth. The same technique applied to encicode words
(instead of ciphertext characters) is used for
stripping additives to relative or absolute
placode. This is foundational, and cited and quoted in
most of the later books.
📑 Prescott, Kyle; “Musician Cryptologists: The
Band of the USS California at Pearl Harbor and Beyond”; in
Proceedings of the 7th International Conference on Historical
Cryptology (HistoCrypt 2024); abstract
and download
Abstract Working from the basement of US Pacific
Fleet Headquarters in Pearl Harbor from 1941, a small team of navy
cryptanalysts and linguists known as the Combat Intelligence Unit (CIU)
provided the US Pacific Fleet Command with timely details of the
capabilities and intentions of the Japanese Imperial Navy (IJN) in the
Pacific. A substantial portion of the CIU was comprised of 20 enlisted
musicians of US Navy Unit Band 16, the band of the USS California
(BB-44), who survived the sinking of their ship in the attack of
December 7, 1941. The musicians were recruited to Combat Intelligence,
retrained to perform tasks related to the deciphering of Japanese Naval
Code JN-25b, and contributed to that unit’s celebrated intelligence
successes of 1942. As the war waged on, several musicians from Band 16
transferred to the Naval Communications Complex at Nebraska Avenue in
Washington DC, and three eventually joined the National Security Agency
(NSA) and served through the height of the Cold War.
🕮 Stripp, Alan; Codebreaker
in the Far East IA;
1993; IA Search only.
- cites Kerckhoffs, p. 105, notes 64 &
65, p.196;
- Additive, p.71, 90, 105, 126, 196.
Web pages
- NSA
Biography of Joe Rochefort; Wikipedia notes it has incorrect birth
year (1898, given elsewhere as 1900-05-12).
- Wikipedia:
Joseph Rochefort
- “Unsealed
75 years after Battle of Midway, by Michael E. Ruane, June 19, 2020,
in WaPo Retropolis.
- The National WWII Museum
- Secret WWII: Spies & Special Ops podcast series YT
playlist Part 1 mentions Station HYPO in intro, release 2025-09-18.
(part 1 discusses Army break of Japanese diplomatic PURPLE machine
slightly, mostly discusses upgrading of Donovan’s OSS at behest of Brit
secret services.)
- Wayback Machine
- NSA Pub.23 “The
Battle of Midway:”AF is Short of Water”, 2004, “How Cryptology
enabled the United States to turn the tide in the Pacific
War.”
- Cryptological Afterthoughts,
excerpts from CRYPTOLOG? the journal of The U.S. Naval Cryptologic
Veterans Association; CAPT Rochefort’s oral history
interview in 1969. 1,
2,
3,
4,
5:
Midway, 6;
7;
- about.com: Americas
Code Breaker: Rochefort’s banishment, Herb Kugel, a continuation of
Americas
Code Breaker (1) (2)
(3)
(4)
Target AF
- DTIC (Defense
Technical Information Center) War College etc theses on adjacent
topics; unclassified unrestricted military academic papers. Many (all
below) shadowed on IA.
- ADA471458
More to the Story- A Reappraisal of U.S. Intelligence Prior to the
Pacific War ACGSC
- ADA264391
Intelligence and Surprise- The Battles of Midway NWC
- ADA417552
Evolution: Advancing Communities of Practice in Naval Intelligence
NPGS
- ADA583353
Navy Information Dominance, the Battle of Midway, and
the Joint Force Commander: It Worked Then, It Needs to Work Now NWC
- ADA351751
Operational Intelligence at the Battle of Midway NWC
- ADA193977
The Japanese Attack on Darwin: 19 Feb 42 : A Case Study in Surprise at
the Operational Level AWC
- ADA505406 A
Comparative Analysis of the Military Leadership Styles of Ernest J. King
and Chester W. Nimitz ACGSC
- ACGSC = Army Command & General Staff College;
NWC = Naval War College; AWC = Army
War College; NPGS = Naval Post Graduate School.
Title {Item Template}
text







 Using IBM
405 Tabulators
Using IBM
405 Tabulators 5 messages in depth
5 messages in depth Difference runs on columns A and E.
Difference runs on columns A and E.

